Hack of Spanish PM’s phone deepens Europe’s spyware crisis | Russia reroutes internet in occupied Ukrainian territory | Meet abortion bans’ new best friend—your phone
Follow us on Twitter. The Daily Cyber Digest focuses on the topics we work on, including cyber, critical technologies & strategic issues like foreign interference.
The Spanish government on Monday said that Prime Minister Pedro Sánchez was hacked with Pegasus software, an Israeli-made digital hacking tool to snoop on phone communication. POLITICO
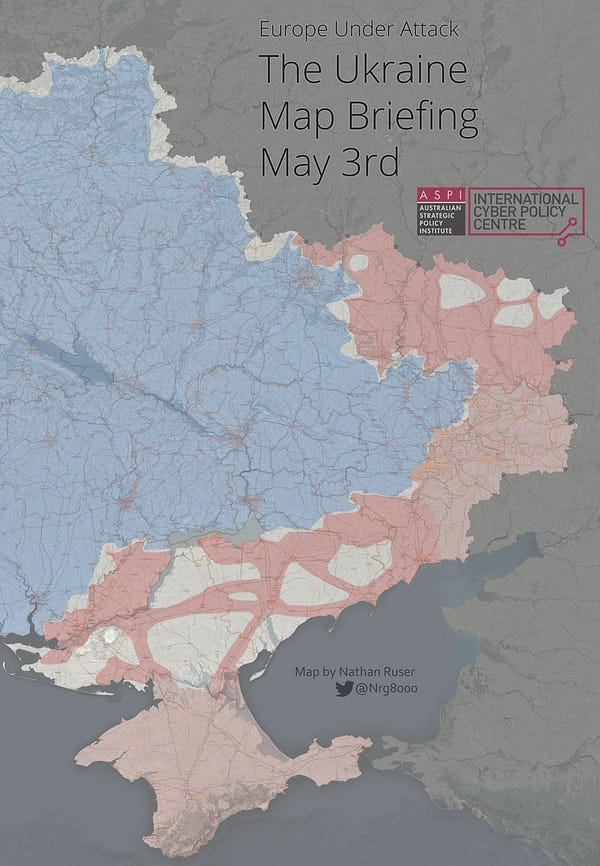
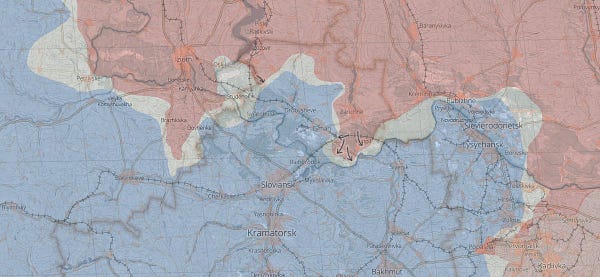
After knocking out the internet service in Kherson, Ukraine, this weekend, Russian forces reinstated service but routed it through Russia’s network instead of Ukrainian telecommunications infrastructure. The Record by Recorded Future
As the line between our digital and physical selves fades, surveillance researchers and reproductive rights advocates increasingly see our data as the next big front in the war on abortion. Mother Jones
ASPI ICPC
Better data needed to improve Indigenous STEM and cyber pathways: ASPI
InnovationAus
Brandon How
Better data and public reporting is needed as a starting point to improve Indigenous recruitment and retention in Defence, particularly around STEM and cyber, a new Australian Strategic Policy Institute report has found.



The World
Japan, U.S. to deepen cooperation in cutting-edge chips
Nikkei Asia
Japan and the U.S. will deepen cooperation in building supply chains for cutting-edge semiconductor devices, amid growing rivalry between Washington and Beijing. The two governments are close to agreeing on cooperation in producing chips more advanced than 2 nanometers, Nikkei has learned. They are also working on a framework to prevent technology leaks, with China in mind.
Ukraine - Russia
Russia reroutes internet in occupied Ukrainian territory through Russian telcos
The Record by Recorded Future
Jonathan Greig
After knocking out the internet service in Kherson, Ukraine, this weekend, Russian forces reinstated service but routed it through Russia’s network instead of Ukrainian telecommunications infrastructure. Ukrainian officials and internet access monitor Netblocks said there was a near-total internet blackout across Kherson on Saturday, knocking out the connectivity of Ukrainian providers like Ukrtelecom, Kyivstar and Volia.
Russia reroutes internet traffic in occupied Ukraine to its infrastructure
Reuters
Max Hunder and Tom Balmforth
Russia has rerouted internet traffic in the occupied Ukrainian region of Kherson through Russian communications infrastructure, the internet service disruption monitor NetBlocks said on Monday. The move appeared aimed at tightening Moscow's grip on a region where it claims it has taken full control.


How Russia benefits from ill-informed social media policies
TechTank
Emma Briant
During this bloody war, the Kremlin’s strategy in the West seeks to benefit by exploiting our fears of censorship. Of course, this obscures the dark irony that Russia tolerates no dissent within its borders, blocking independent media and platforms like Facebook. Just as stark is the hypocrisy of its effort to energize concerns about Western imperialism while waging an aggressive imperialist war against its neighbor.
Ukraine’s digital fight goes global
Foreign Affairs
Elisabeth Braw
A somewhat conventional war is underway in Ukraine, featuring organized and professional soldiers, a chain of command, advanced weapons such as drones and tanks, and state-crafted tactics and strategy. But a parallel war is also taking place, mostly in cyberspace, fueled by foreign volunteers fighting for either Russia or Ukraine.
Multiple government hacking groups stay busy targeting Ukraine and the region, Google researchers say
CyberScoop
AJ Vicens
Government-backed hackers from Russia, China and Belarus have been behind a series of a series of hacking campaigns in recent weeks targeting government, industry, journalists, politicians and others, according to the latest update from Google’s Threat Analysis Group.In cyber conflict, Ukraine has an underdog advantage over Russia
The Washington Post
Joseph Marks
There have been big Russian hacks, to be sure — but none that played a decisive role in the military conflict. Ukraine, meanwhile, has more than held its own, both in defending its own digital assets and striking back at Russia in cyberspace.


Australia


China
Chinese "Override Panda" hackers resurface with new espionage attacks
The Hacker News
Ravie Lakshmanan
A Chinese state-sponsored espionage group known as Override Panda has resurfaced in recent weeks with a new phishing attack with the goal of stealing sensitive information. "The Chinese APT used a spear-phishing email to deliver a beacon of a Red Team framework known as 'Viper,'" Cluster25 said in a report published last week.
Beijing's Ukrainian battle lab
War On The Rocks
David Finkelstein
Among those observing the Russian military’s ongoing operations in Ukraine, few will be watching and assessing its performance more intensely than those in the Chinese People’s Liberation Army (PLA). Analyzing the wars of other countries continues to play an important role in Beijing’s decision-making about military modernization, along with the PLA’s own field experiments and its increasing use of big data, AI, and simulations.
USA
Researchers find over 400 vulnerabilities in defense industrial base bug bounty effort
The Record by Recorded Future
Martin Matishak
A year-long bug bounty program that scrutinized a fraction of the massive U.S. defense industrial base turned up more than 400 valid vulnerabilities, the effort’s organizers announced Monday. Nearly three hundred security researchers from bug bounty vendor HackerOne participated in the 12-month exercise, dubbed the Defense Industrial Base Vulnerability Disclosure Program (DIB-VDP) Pilot, and made 1,015 reports as they examined the networks of participating defense contractors — 401 of vulnerabilities were deemed actionable and required remediation, according to the firm.
Pentagon contractors go looking for software flaws as foreign hacking threats loom
CNN Politics
Sean Lyngaas
A year-long Pentagon pilot program found an array of software vulnerabilities at dozens of defense contractors as Russian and Chinese hackers continue to try to steal sensitive data from the US defense industrial base. The goal of the "Vulnerability Disclosure Program" (VDP) is to find and fix flaws in the email programs, mobile devices and industrial software used by Pentagon contractors before malicious hackers can take advantage of the vulnerabilities.
To win the next war, the Pentagon needs nerds
WIRED
Will Knight
Data scientists, coders, and other techies could prove decisive in future conflicts—if Uncle Sam can recruit them. There are many ways AI and other technology could benefit the US military besides aiding with intelligence gathering and analysis or making weapons smarter.
How AI would — and wouldn't — factor into a U.S.-Chinese war
War On The Rocks
Alex Stephenson and Ryan Fedasiuk
The Pentagon is getting a new AI Strategy. Between shaping ethical norms for AI and establishing a new Chief Data and AI Officer, it’s clear top brass have big plans for the technology, though the report is light on the details. Released in 2018, the last AI Strategy laid the scaffolding for the U.S. military’s high-tech competition with China. But over the past four years one thing has become apparent: The United States needs a balanced approach to AI investment — one that doesn’t simply guard against threats, but also imposes costs on a Chinese force that sees AI as the key to victory.
Where is China-US technology competition going?
The Diplomat
Dingding Chen and Wang Lei
In recent years, as part of its strategy to contain or delay the rise of China, the U.S. government has taken a series of measures and sanctions against Chinese technology companies. The U.S. Congress, the government, and key think tanks have released 209 bills, policies, and reports concerning science and technology policies toward China. Such policies include sanctions on China’s high-tech companies, regulations over key cutting-edge technologies, and restrictions on the training of STEM talents.
CDC tracked millions of phones to see if Americans followed COVID lockdown orders
VICE
Joseph Cox
The Centers for Disease Control and Prevention (CDC) bought access to location data harvested from tens of millions of phones in the United States to perform analysis of compliance with curfews, track patterns of people visiting K-12 schools, and specifically monitor the effectiveness of policy in the Navajo Nation, according to CDC documents obtained by Motherboard. The documents also show that although the CDC used COVID-19 as a reason to buy access to the data more quickly, it intended to use it for more general CDC purposes.
South & Central Asia
New regulations in India require orgs to report cyber incidents within 6 hours
Dark Reading
The Indian Computer Emergency Response Team (CERT-In) issued new cyber incident reporting guidelines, including the requirement for service providers, intermediaries, data centers, corporations, and government agencies to report cyber incidents to the regulator within six hours.
Europe
Hack of Spanish PM’s phone deepens Europe’s spyware crisis
POLITICO
Vincenr Manancourt
The Spanish government on Monday said that Prime Minister Pedro Sánchez was hacked with Pegasus software, an Israeli-made digital hacking tool to snoop on phone communication. Sánchez as well as Defense Minister Margarita Robles fell victim to the malicious software in May and June 2021, in what Madrid called an "illegal and external" intrusion of government communication.
Over 200 Spanish mobile numbers ‘possible targets of Pegasus spyware’
The Guardian
Stephanie Kirchgaessner and Sam Jones
More than 200 Spanish mobile numbers were selected as possible targets for surveillance by an NSO Group client believed to be Morocco, according to the data leak at the heart of the Pegasus project. Details of the scale of the apparent targeting came as Spain’s highest criminal court opened an investigation into how the mobile phones of the prime minister, Pedro Sánchez, and the defence minister, Margarita Robles, came to be infected with Pegasus spyware last year.
The Middle East
Israel keen to set up cyber 'Iron Dome' to curb rise in attacks
Reuters
Steven Scheer
Israel's government on Monday ordered communications firms to step up their cyber security efforts in the wake of a rise in attempted hacking attacks. New regulations are currently being implemented in which mandatory and unified standards will have to be met.
Africa
Only two African countries sign ‘The Declaration For the Future of the Internet’
News24
Lenin Ndebele
Cabo Verde and Niger are the only two African countries that have signed 'The Declaration for the Future of the Internet'. The declaration comes at a time when the internet is providing opportunities never seen before for people around the world to connect socio-economically. However, despite this positivity, the internet has also provided policy challenges.
Gender & Women in Cyber
Meet abortion bans’ new best friend—your phone
Mother Jones
Lil Kalish
As the line between our digital and physical selves fades, surveillance researchers and reproductive rights advocates increasingly see our data as the next big front in the war on abortion. Law enforcement has new tricks to land convictions for miscarriages or post-ban abortions; anti-abortion activists are making sophisticated updates to tried-and-true methods of stalking, harassment, and disinformation.
Data broker is selling location data of people who visit abortion clinics
VICE
Joseph Cox
A location data firm is selling information related to visits to clinics that provide abortions including Planned Parenthood facilities, showing where groups of people visiting the locations came from, how long they stayed there, and where they then went afterwards, according to sets of the data purchased by Motherboard.
Big Tech
Apple faces E.U. antitrust charges over Apple Pay
The New York Times
Adam Satariano
European Union regulators said on Monday that Apple had broken antitrust laws by unfairly undercutting companies whose payment services competed with Apple Pay, in the latest crackdown by European authorities on the world’s largest tech companies.
Grindr user data was sold through ad networks
The Wall Street Journal
Byron Tau and Georgia Wells
The precise movement of millions of users of the gay-dating app Grindr were collected from a digital advertising network and made available for sale. The information was available for sale since at least 2017, and historical data may still be obtainable.
Twitter latest filing admits to risk of losing advertisers and staff due to Musk takeover
TechCrunch
Sarach Perez
Just ahead of its presentation to media ad buyers later this week at the 2022 NewFronts, Twitter acknowledged in a new SEC filing that its core advertising business could now be at risk as a result of the Elon Musk takeover, in addition to employee hiring and retention efforts and other factors.
Facebook-owner Meta opens access to AI large language model
Reuters
Elizabeth Culliford
Facebook-owner Meta Platforms Inc (FB.O) is opening up access to a large language model for artificial intelligence research, the social media company said on Tuesday. Meta said its model was the first 175-billion-parameter language model to be made available to the broader AI research community.
Another firing among Google’s A.I. brain trust, and more discord
The New York Times
Daisuke Wakabayashi and Cade Metz
Less than two years after Google dismissed two researchers who criticized the biases built into artificial intelligence systems, the company has fired a researcher who questioned a paper it published on the abilities of a specialized type of artificial intelligence used in making computer chips.
Google offers $1.5M bug bounty for Android 13 Beta
Dark Reading
Tara Seals
Google has expanded its bug-bounty program to offer a whopping $1.5 million for a top-notch Android 13 Beta exploit – specifically, for a hack of the Titan M security chip that ships with Pixel phones.
Big tech lobbyists use trans people to avoid antitrust regulation
VICE
Evan Greer
Washington is on the verge of doing something big: finally passing meaningful legislation to rein in the monopoly power and abusive practices of Big Tech giants. Feeling the heat, Silicon Valley’s lobbyists have sunk to a new low: using the safety of trans and queer people as a wedge issue to undermine tech reform bills that would help, not harm, the LGBTQ+ community.
Misc
Crypto hackers stole more than $370 million in April alone
VICE
Lorenzo Franceschi-Bicchierai
In April alone, hackers stole more than $370 million in crypto from several web3 projects, according to a cybersecurity firm, with nearly $100 million being stolen over the weekend. In the last month, there were 31 hacks affecting crypto or web3 projects, including Beanstalk, Fei Protocol, Deus Finance, and Bored Ape Yacht Club.
Events
Charting the future of big tech accountability
New America
Big Tech accountability has come a long way since Ranking Digital Rights’ inaugural report in 2015. More than ever, the companies we rank make explicit commitments to human rights, disclose how they handle government demands, and clearly describe their security measures. But the 2022 Big Tech Scorecard shows that there’s still a long way to go—and a lot we don’t know.
Research
What if smart cities encouraged stupid risks?
DGAP MEMO
Valentin Weber
For years, countries have endorsed norms of responsible state behavior in cyberspace, claiming they would refrain from conducting cyberattacks on critical national infrastructure and would disclose system vulnerabilities whenever possible. While these norms have been politically agreed upon by all UN member states, they have been widely violated.
Jobs
The Sydney Dialogue - Senior Events Coordinator
ASPI ICPC
The Australian Strategic Policy Institute (ASPI) is currently recruiting for an experienced events professional to coordinate the planning and logistics of the second iteration of ASPI’s Sydney Dialogue - the world’s premier summit on emerging, critical and cyber technologies.
ICPC Senior Analyst or Analyst - China
ASPI ICPC
ASPI’s International Cyber Policy Centre (ICPC) has a unique opportunity for exceptional and experienced China-focused senior analysts or analysts to join its centre. This role will focus on original research and analysis centred around the (growing) range of topics which our ICPC China team work on. Our China team produces some of the most impactful and well-read policy-relevant research in the world, with our experts often being called upon by politicians, governments, corporates and civil society actors to provide briefings and advice.