NEW REPORTS: ASPI ICPC updates the China Tech Map Project | Trump’s TikTok, WeChat actions revoked by Biden | Australia urged to follow Biden’s lead on cyber attacks
Follow us on Twitter. The Daily Cyber Digest focuses on the topics we work on, including cyber, critical technologies & strategic issues like foreign interference.
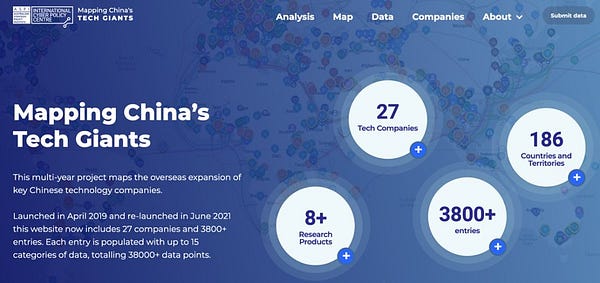
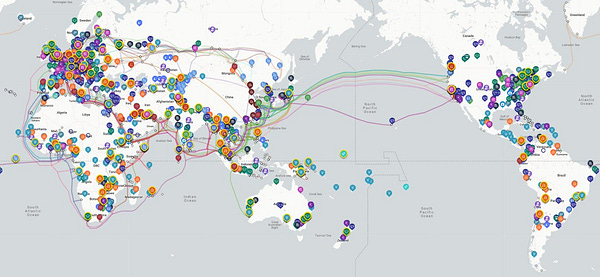
Mapping China’s Technology Giants is a multi-year project by ASPI’s International Cyber Policy Centre that tracks the overseas expansion of key Chinese technology companies. This data-driven project, and the accompanying database and research products, fill a research and policy gap by building understanding about the global trajectory and impact of China’s largest companies working across the internet, telecommunications, artificial intelligence, surveillance, e-commerce, finance, biotechnology, big data, cloud computing, smart city and social media sectors. Today, we’ve relaunched our project with major data updates, new analytical products and two new reports. Here’s a summary of what you can now find on our website: ‘Mapping China’s Tech Giants: Covid-19, supply chains and strategic competition’.
President Biden revoked a Trump -era attempt to ban Chinese-owned apps TikTok and WeChat, substituting Wednesday an executive order mandating a broad review of apps controlled by foreign adversaries to determine whether they pose a security threat to the U.S. The Wall Street Journal
The Morrison government is being urged to follow US President Joe Biden’s lead and make combating ransomware a national priority comparable to terrorism, as big Australian companies grapple with increasingly frequent and sophisticated attempts to extort them. The Australian Financial Review
ASPI ICPC

China’s surveillance tech suffers international backlash
Financial Times
@narkoyanagi @JKynge & Kenji Kawase
The Australian Strategic Policy Institute has a trenchant new report on China’s data ecosystem, providing insights into how Beijing’s party-state apparatus collects data around the world.Read our new report ‘Mapping China’s Technology Giants: Supply chains and the global data collection ecosystem’.
It was one hour of global internet disruption ... but it could get a lot worse
The Sydney Morning Herald
@techstrat_99
On Tuesday night, many of the world’s big websites went down. E-commerce sites, entertainment platforms, online service providers, the British government’s websites and media outlets – including this one – were suddenly inaccessible.. The company, Fastly, is what’s known as a content delivery network (CDN). CDNs are used primarily to deliver faster and therefore “better” internet more cheaply by distributing the internet load to servers closer to the user..Tuesday’s outage points to a significant risk in how the internet functions today. Namely, that the position of CDNs in the infrastructure of today’s internet leads to increased risk for systemic failure.
Experts unclear how Australian encryption laws were used in global crime bust
The Age
@LisaVisentin
Controversial Australian encryption-busting laws played a key role in bringing down hundreds of organised crime figures, with federal police monitoring communications on US soil. But legal and cyber experts say it is unclear exactly how the laws were used, and concerns remain about the scope of the legislation passed in 2018.. Tom Uren, a cyber policy expert at the Australian Strategic Policy Institute, said the operation had gone a long way to vindicating the TOLA laws, which were rushed through the Parliament on the last sitting week in 2018. But he said more transparency was needed over exactly how the powers were applied. “This operation was a tremendous success. This is actually a fantastic application of police powers to achieve something good. But I think it would be useful if they were explicit about which powers they did use [under the Act],” Mr Uren said.
World
US and Europe to forge tech alliance amid China’s rise
POLITICO
@markscott82 @jacopobarigazzi
The European Union and the United States will announce a wide-ranging partnership around technology and trade next week in an attempt to push back against China and promote democratic values, according to two EU officials and draft conclusions for the upcoming EU-U.S. summit seen by POLITICO.
Will Europe sign up to Joe Biden’s plan to counter China? The Financial Times



Major internet outage ‘shows infrastructure needs urgent fixing’
The Guardian
@alexhern @dansabbagh
One of the world’s biggest web outages should act as a “wake-up call” that internet infrastructure has become dangerously over-centralised and lacks resilience, security experts have warned.
Fastly blames global internet outage on software bug Associated Press
Australia
Australia urged to follow Biden’s lead on cyber attacks
The Australian Financial Review
@Maxepmason
The Morrison government is being urged to follow US President Joe Biden’s lead and make combating ransomware a national priority comparable to terrorism, as big Australian companies grapple with increasingly frequent and sophisticated attempts to extort them.. The attack put ransomware firmly at the top of the G7 agenda this weekend. Earlier this week, US National Security Adviser Jake Sullivan said Mr Biden will seek an action plan on combating ransomware at the G7 summit this weekend.
Six Australians charged by FBI over alleged links to underworld app An0m
The Guardian
@ninobucci
The FBI has charged six Australians over their alleged links to An0m encrypted devices, with the accused men ranging from administrators, who allegedly ran the network, to distributors, who allegedly controlled teams that provided the devices to criminals.
AFP didn't create ANoM crime app, only involved 'just before' release
The New Daily
@JoshButler
The Australian Federal Police have admitted they didn’t actually “create” the encrypted app used by criminals but secretly run by the FBI, and got involved only “just before” it was released to crooks. The AFP has clarified that it was behind the capability to decrypt and read the messages on the ANoM app, but didn’t actually build the app. In fact, ANoM was initially developed – and then given to police – by criminals who had worked on previous encrypted communications that had been busted by the FBI, according to newly-unsealed court documents filed in US courts.
Protecting children online
Policy Forum
@dogtormortensen & Samuel Bashfield
Despite the Australian Government’s efforts to safeguard children from exploitation, child sexual abuse content is flourishing unabated on Australia’s Child sexual abuse content is flourishing unabated on one of Australia’s Top-Level Domains and must be stopped, James Mortensen and Samuel Bashfield write.
China
Apple Worked With Company Tied To Xinjiang
BuzzFeed News
@meghara
Apple and Warren Buffett’s Berkshire Hathaway have done business with a Chinese wind energy giant linked to controversial government and labor programs in Xinjiang, where the US and other countries say China is carrying out a genocide of Muslim minorities.
Some Apple Suppliers in China Tell Ethnic Minorities: Don’t Bother Applying For Jobs
The Information
@waynema
Some of the companies in China that supply Apple with parts for its devices are willing to use workers from the predominantly Muslim group known as Uyghurs, as part of government-sponsored labor programs widely criticized as coercive. But Uyghurs and other marginalized Chinese minorities need not apply for jobs on the open market to many of those same suppliers. The Information found more than 100 online ads for production line jobs containing discriminatory language across more than 30 companies in Apple’s supply chainRead our report 'Uyghurs for Sale'
Apple's new 'private relay' feature will not be available in China
Reuters
@StephenNellis @peard33
Apple Inc on Monday said a new "private relay" feature designed to obscure a user's web browsing behavior from internet service providers and advertisers will not be available in China for regulatory reasons.
Huawei reveals 'cybersecurity framework' with launch of China transparency centre
ZDNet
@eileenscyu
Huawei Technologies has kicked into PR overdrive, pledging its commitment to cybersecurity with the opening of its latest transparency centre in Dongguan, China. It also releases the "security baseline framework" that the Chinese tech vendor says is adopted for its products, outlining requirements for implementation and compliance of legal and regulatory requirements.
China's tech workers pushed to limits by surveillance software
Nikkei Asia
@hk_nikkisun
A vicious cycle of monitoring and overwork is fueling productivity -- and backlash.
Tech Crackdown Hits Chinese Stocks, Just Not in China
The Wall Street Journal
@yuenok
Beijing’s effort to rein in its internet giants has mostly affected the share price of companies listed offshore.
USA
Trump’s TikTok, WeChat Actions Targeting China Revoked by Biden
The Wall Street Journal
@johndmckinnon @learyreports
President Biden revoked a Trump-era attempt to ban Chinese-owned apps TikTok and WeChat, substituting Wednesday an executive order mandating a broad review of apps controlled by foreign adversaries to determine whether they pose a security threat to the U.S. The new order doesn’t target any companies specifically, but creates the potential for an even broader crackdown on Chinese-owned apps than the Trump administration orders it replaces by mandating a review of all software applications with potential ties to countries such as China.
FACT SHEET: Executive Order Protecting Americans’ Sensitive Data from Foreign Adversaries
The White House
The Biden Administration is committed to promoting an open, interoperable, reliable and secure Internet; protecting human rights online and offline; and supporting a vibrant, global digital economy. Certain countries, including the People’s Republic of China (PRC), do not share these values and seek to leverage digital technologies and Americans’ data in ways that present unacceptable national security risks while advancing authoritarian controls and interests.
Deputy Defense Secretary Outlines Responsible AI Tenets in New Memo
Nextgov
@mila_jasper
In a department wide memo signed last week, Deputy Defense Secretary Kathleen Hicks enumerated foundational tenets for responsible AI, reaffirmed the ethical AI principles the department adopted last year, and mandated the JAIC director start work on four activities for developing a responsible AI ecosystem.
Chinese National Pleads Guilty to Illegal Exports to Northwestern Polytechnical University
US Department of Justice
In late April, Massachusetts-based businessman Qin Shuren became the latest person to plead guilty in the Justice Department’s crackdown on the illegal export of strategic technologies. Qin’s company, LinkOcean Technologies, falsified documentation to send a Chinese military-affiliated university some $100,000 worth of equipment, including hydrophones, sonobuoys, side-scan sonars, and even an autonomous underwater vehicle (AUV). The case is just one part of a long trail of open-source evidence that illustrates a larger issue: U.S. technology being used to advance Chinese military ends.
How China Steals US Tech to Catch Up in Underwater Warfare
Defense One
@conanwhatisbest @peterwsinger
From legal filings to a Chinese lab’s website, open-source documents provide an illuminating trail.
North-East Asia
Japan vows to tackle Chinese ‘coercion’
The Australian
@bennpackham @Adam_Creighton
Senator Payne and Mr Dutton, in the statement issued late Wednesday with the Japanese officials, said the countries were committed to “opposing coercion and destabilising behaviour by economic means, which undermines the rules-based international system”. “We will explore deeper collaboration, including to address illicit technology transfer, build resilience in relevant supply chains, increase defence industrial base collaboration, and promote the application of international law and agreed norms in state conduct in cyberspace,” the statement read. “We will deepen co-operation on cyber and critical technology, including to develop our bilateral partnership, with a view to advancing collaboration on relevant themes such as research and development, regional capacity building, and industry resilience.” The focus on supply chains and critical technology comes as the Biden administration concludes a 100-day review into the issue.
Japanese Government Agencies Suffered Cyber Attack Exposing Proprietary Data
CPO Magazine
Several Japanese government agencies reportedly suffered data breaches originating from Fujitsu’s “ProjectWEB” information sharing tool.
Emerging Military Technologies and a Future Taiwan Strait Conflict
The Diplomat
@nktpnd
The Diplomat’s Asia Geopolitics podcast host Ankit Panda speaks Franz-Stefan Gady, a research fellow at the International Institute for Strategic Studies, about how emerging technologies might affect a future conflict between the United States and China in the Taiwan Strait. The podcast discusses Gady’s new report for IISS’s 2021 Asia-Pacific Regional Security Assessment.
South and Central Asia
In Pakistan, pro-government ‘fact checkers’ attack journalists
Coda Story
@ramshajahangir
An army of online volunteers has come to the aid of Prime Minister Imran Khan, lambasting reporters and picking apart stories that criticize the government.
Twitter restricts accounts in India to comply with government legal request
TechCrunch
@refsrc
Twitter disclosed on Monday that it blocked four accounts in India to comply with a new legal request from the Indian government.
UK
Stop forced labour in China, G7 told
The Times
The independent anti-slavery commissioner has called on G7 countries to ban state-controlled forced labour and use the debate about China as a catalyst to stamp out modern slavery.
Read our report 'Uyghurs for Sale'.
The Americas
El Salvador adopts bitcoin as legal tender after passing law
CNBC
@ArjunKharpal
El Salvador has become the first country to adopt bitcoin as legal tender. Lawmakers in the Central American country’s Congress voted by a “supermajority” in favor of the Bitcoin Law, receiving 62 out of 84 of the legislature’s vote.
Middle East
Secretive Israeli cyber firm selling spy-tech to Saudi Arabia
Haaretz.com
@gurmegiddo
Quadream, led by a former Israeli military intelligence official, and the phone-hacking tech was sold to Saudi Arabia. It allows clients a ‘zero-click’ hack into a target's iPhone.
Misc
Apple and Google Refuse to Say Whether Citizen Bounty Hunt Violated Policies
VICE News
@josephfcox
Apple updated it's App Store policy about reporting alleged criminal activity after the incident, but has not given any specifics on why it made these changes.
Facebook plans first smartwatch for next summer with two cameras
The Verge
@alexeheath
Facebook is taking a novel approach to its first smartwatch, which the company hasn’t confirmed publicly but currently plans to debut next summer. The device will feature a display with two cameras that can be detached from the wrist for taking pictures and videos that can be shared across Facebook’s suite of apps, including Instagram, The Verge has learned.
Young Creators Are Burning Out and Breaking Down
The New York Times
@taylorlorenz
Gen Z creators are struggling with the challenges that come with building, managing and monetizing a following online.
Events


Research
Comparing the United States’ and China’s Leading Roles in the Landscape of Science
Center for Security and Emerging Technology
Using CSET’s new Map of Science to examine clusters of research publications, this data brief presents a comparative analysis of U.S. and Chinese research publication outputs. The authors find that global competition outcomes differ depending on the level of granularity when comparing research publication data. In a granular view of global scientific research, the United States and China together dominate almost two-thirds of the research publication output, with the rest of the world leading in more than one-third of publication output. In a general view of global scientific research, only China and the United States appear as leaders in research output.
Jobs
ICPC Analyst or Senior Analyst - Cyber & technology
ASPI ICPC
ASPI’s International Cyber Policy Centre (ICPC) has a unique opportunity for an exceptional cyber-security or technology focused analyst or senior analyst to join its centre in 2021. Please note that interviews have commenced for this position and will continue until the end of June. This role will focus on policy relevant cybersecurity analysis, informed public commentary and either original data-heavy research and/or technical analysis. Analysts usually have around 7-15 years work experience. Senior analysts usually have a minimum of 15 years relevant work experience and tend to be involved in staff and project management, fundraising and stakeholder engagement.