US-EU tech off to bad start | Russian hackers leveled $5.9 million ransomware attack on an Iowa farming co-op | New ASPI Report: A 3D deep dive into the India-China border
Follow us on Twitter. The Daily Cyber Digest focuses on the topics we work on, including cyber, critical technologies & strategic issues like foreign interference.
An attempt to build a transatlantic framework for cooperating on trade and technology looks cursed before it’s even started. Even before a transatlantic flare-up over submarines, which now looks likely to delay the first session of the Trade and Tech Council planned for September 29, Washington and Brussels had widely diverging visions of what they wanted out of this new diplomatic initiative. POLITICO
Russian hackers leveled a ransomware attack on an Iowa farming co-op and demanded $5.9 million to unlock the computer networks used to keep food supply chains and feeding schedules on track for millions of chickens, hogs and cattle. The Washington Post
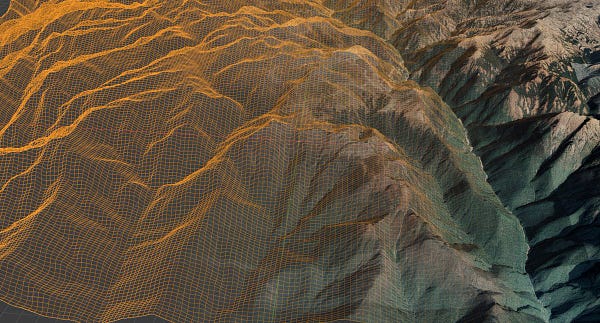
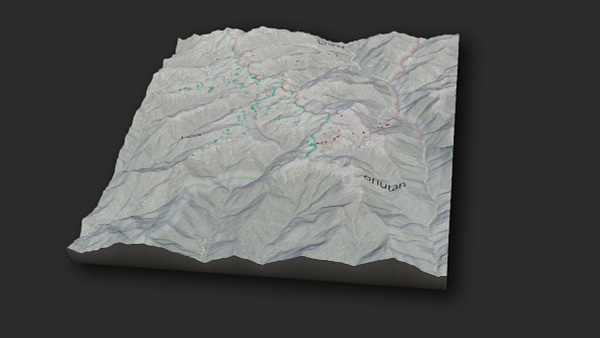
ASPI’s International Cyber Policy Centre has built 3D satellite imagery — through the collection and analysis of new satellite imagery and using open-source datasets we have compiled (such as geolocated military & infrastructure positions) — to help assess current developments along the India–China border. ASPI ICPC
ASPI ICPC
New Report: A 3D deep dive into the India-China border
@Nrg8000 @BaniGrewal @DaniellesCave
ASPI’s International Cyber Policy Centre has built 3D satellite imagery — through the collection and analysis of new satellite imagery and using open-source datasets we have compiled (such as geolocated military & infrastructure positions) — to help assess current developments along the India–China border. India–China border tensions have become one of the Indo-Pacific’s defining territorial disputes. The Chinese military’s activities on the contested border have been one of the key drivers behind the shift in the Indian public’s and government’s assessments of India’s relationship with China. The result has been a faster convergence in regional security and strategic policy directions. One obvious manifestation of this is the growing Quad partnership between New Delhi, Tokyo, Canberra and Washington. Events and activities on and around this contested border are important to understand, not only for regional dynamics but also because of the risk of conflict and escalation.


The five-domains update
The Strategist
@hillarymansour5 @KhweziSays @MatthewRPage Jackson Schultz
The new AUKUS alliance could also be leveraged against ‘hybrid threats’ posed by cyber operations, with ASPI’s Fergus Hanson and Danielle Cave contending that Australia is ‘well placed to turbocharge its strategic tech capability’.
World
Why the Quad has a big role in the new techno-diplomacy
Australian Financial Review
@jen_jackett
The Quadrilateral Security Dialogue will build more momentum when leaders from Australia, Japan, India, and the US meet on Friday, Washington time, for their second meeting this year. There are strong strategic imperatives pulling Quad nations together. The US is looking to reaffirm its commitment to the Indo-Pacific region, technological disruption is redistributing political power, and the human and economic impacts of COVID-19 continue to reverberate.
As Quad focuses on tech, the debate on standard setting
Hindustan Times
Arjun Gargeyas
The control of critical technologies and their supply chains remain essential for all States to project their geopolitical influence. However, having a grip on the governance mechanism of these critical technologies in the form of technical standards can be a gamechanger in the geostrategic field.CNAS Press Note: The Quad Heads to the White House
Center for a New American Security
@LisaCurtisDC @MartijnRasser @jacobstokes Zachary Durkee
On Friday, the four leaders of the Quadrilateral Security Dialogue—India's Narendra Modi, Japan's Yoshihide Suga, Australia's Scott Morrison, and President Biden—will meet in-person for the first time at the White House.
Facebook Grew Marketplace to 1 Billion Users. Now Scammers Are Using It to Target People Around the World.
ProPublica
@CraigSilverman @ACInvestigates @peterelkind
Facebook’s Marketplace is unquestionably a business success. It hit 1 billion users a month this spring, and the company recently told investors that it’s one of its most promising new sources of revenue. Facebook says it protects users through a mix of automated systems and human reviews. But a ProPublica investigation based on internal corporate documents, interviews and law enforcement records reveals how those safeguards fail to protect buyers and sellers from scam listings, fake accounts and violent crime.
China
SoftBank to Take ‘More Cautious’ Tack as It Cuts Deals in China
Bloomberg
@arascouet @pashakun
SoftBank Group, one of the biggest foreign investors in China, plans to take a more cautious approach to backing the country’s startups but will continue to cut deals, according to Chief Operating Officer Marcelo Claure. The Japanese conglomerate’s stock came under pressure in recent weeks as a widening crackdown by Beijing regulators on China’s tech sector battered the value of some of its biggest investments, including Alibaba Group Holding Ltd. Now the debt crisis at troubled developer China Evergrande Group is threatening broader fallout in the world’s second-largest economy.
Hikvision Has "Highest Level of Critical Vulnerability," Impacting 100+ Million Devices
IPVM
@IPVMJuanHon
Hikvision has admitted a 9.8 vulnerability that is "the highest level of critical vulnerability—a zero-click unauthenticated remote code execution" per the researcher, Watchful_IP, who discovered this. IPVM estimates it impacts 100+ million devices.
USA
Russian hackers target Iowa grain co-op in $5.9 million ransomware attack
The Washington Post
@jacobbogage @lreiley
Russian hackers leveled a ransomware attack on an Iowa farming co-op and demanded $5.9 million to unlock the computer networks used to keep food supply chains and feeding schedules on track for millions of chickens, hogs and cattle. Fort Dodge-based New Cooperative, a member-owned alliance of farmers that sells corn and soy products, contained the breach and developed a workaround to continue accepting grain shipments and distributing feed, a person close to the company told The Washington Post, speaking on the condition of anonymity to discuss sensitive information.
Crypto Channels Targeted in Biden’s Fight Against Ransomware
Bloomberg
@KartikayM @JenniferJJacobs
The Biden administration plans a fresh campaign against ransomware attacks through sanctions to cut off criminals’ cryptocurrency pipelines, and it urged companies to report extortion attempts and better protect themselves from them.
US imposes sanctions on crypto exchange in ransomware clampdown
Financial Times
@MsHannahMurphy
The US Treasury has imposed sanctions on a cryptocurrency exchange that it says allowed ransomware hackers to launder extortion payments from victims, in one of its most significant interventions to date against a digital asset group. Working together with the FBI, the US Treasury’s Office of Foreign Assets Control announced the curbs on an exchange called SUEX, which it said deliberately “facilitated illicit activities for [its] own illicit gains”. The sanctions block US citizens and companies from transacting with the group, with penalties that include fines.
Treasury Department will sanction crypto exchanges that help channel payments to hackers
The Washington Post
@GerritD
The U.S. government is stepping up its efforts to disrupt the infrastructure hackers use to make money from breaking into and holding hostage computer networks, announcing sanctions against one virtual currency exchange and warning U.S. companies it could be legally risky for them to pay off hackers that hit their systems.
CISA, FBI, and NSA Release Joint Cybersecurity Advisory on Conti Ransomware
Cybersecurity and Infrastructure Security Agency
CISA, the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) have released a joint Cybersecurity Advisory (CSA) alerting organizations of increased Conti ransomware attacks. Malicious cyber actors use Conti ransomware to steal sensitive files from domestic and international organizations, encrypt the targeted organizations’ servers and workstations, and demand a ransom payment from the victims.
Zoom’s Nearly $15 Billion Deal for Five9 Under U.S. Government Review Over China Ties
The Wall Street Journal
@Kate_OKeeffe @aatilley @dawnmlim
A Justice Department-led panel is investigating Zoom Video Communications Inc.’s deal to buy an American customer-service software company, citing potential national-security risks posed by the U.S. videoconferencing giant’s China ties.
U.S. government buying risky Chinese drones
Axios
@lachlan
Federal law enforcement agencies are purchasing surveillance drones from a Chinese company the Pentagon has deemed a potential national security threat, Axios has learned.
A Botched Drone Strike in Kabul Started With the Wrong Car
The New York Times
@EricSchmittNYT
U.S. military officials have insisted since the last American troops withdrew from Afghanistan last month that they would be able to detect and attack Islamic State or Qaeda threats in the country from afar. But an errant drone strike that killed 10 civilians, including seven children, in Kabul on Aug. 29 calls into question the reliability of the intelligence that will be used to conduct the operations.
Trump Campaign Knew Lawyers’ Voting Machine Claims Were Baseless, Memo Shows
The New York Times
@alanfeuer
Two weeks after the 2020 election, a team of lawyers closely allied with Donald J. Trump held a widely watched news conference at the Republican Party’s headquarters in Washington. At the event, they laid out a bizarre conspiracy theory claiming that a voting machine company had worked with an election software firm, the financier George Soros and Venezuela to steal the presidential contest from Mr. Trump.
Google to Spend $2.1 Billion on Manhattan Office Building
The New York Times
@matthewhaag @nicole_hong
Google announced on Tuesday that it would spend $2.1 billion to buy a sprawling Manhattan office building on the Hudson River waterfront, paying one of the largest prices in recent years for an office building in the United States and providing a jolt of optimism to a real estate industry lashed by the pandemic.
CIOs Team Up With Other Executives to Counter Cyber Threats
The Wall Street Journal
@JimRundle
The rapid pace of cyberattacks and shifting government rules around how companies must respond to hacks mean chief information officers must work with other executives to effectively respond, according to one of Google’s most senior security specialists. Heather Adkins, senior director of information security at the Alphabet Inc. -owned tech giant, said that CIOs must work closely with other executives such as chief risk and chief information security officers in order to build lasting and resilient technology architecture.
Mandatory reporting of cyber hacks gets a thumbs-up from Mayorkas
The Washington Post
@Joseph_Marks_
Homeland Security Secretary Alejandro Mayorkas has given a nod to new hacking reporting requirements for certain businesses. The mandates, if passed, would be among the most significant new cyber requirements for industry in years.
U.N. chief says weapons that can pick own targets ‘should be banned’
The Washington Times
@guyjtaylor
U.N. Secretary-General Antonio Guterres laid down a marker Tuesday for the United States and other nations pursuing the development of weaponry that uses artificial intelligence, asserting that weapons capable of picking their own targets “should be banned.”
Tim Cook says employees who leak memos do not belong at Apple, according to leaked memo
The Verge
@ZoeSchiffer
Tim Cook sent an email to Apple employees Tuesday evening about an all-hands meeting that leaked to The Verge last week. He said the company is doing “everything in our power to identify those who leaked” and noted that “people who leak confidential information do not belong” at Apple.
Facebook Paid the FTC Billions to Personally Protect Zuckerberg, Lawsuit Claims
Gizmodo
@whitkimball
A hulking lawsuit made public this week accuses Facebook’s board of agreeing to overpay the Federal Trade Commission billions of dollars in exchange for not personally suing CEO Mark Zuckerberg over the 2018 Cambridge Analytica data leak scandal.
Texas sued over terrible social media law
The Verge
@thedextriarchy
NetChoice and the Computer & Communications Industry Association (CCIA) have sued to stop Texas from enforcing HB 20, a new law barring large social media companies from banning users or removing content based on the “viewpoint” of the user. The tech industry groups’ suit comes two weeks after Texas Governor Greg Abbott signed the bill, and it follows a lawsuit that successfully blocked a similar rule in Florida.
New Zealand
Concern over ‘censorship’ rules of NZ-Chinese news site
Newsroom
@SamSachdevaNZ @EmanuelStoakes
An influential Chinese-language media outlet in New Zealand warned its users their information could be shared with 'relevant state agencies' if they violated Chinese laws.
South Asia
Chinese Hackers Target Indian Agency, Media Company, Report Says
Bloomberg
@jamietarabay
Chinese state-sponsored hackers are believed to have infiltrated and stolen data from an Indian government agency responsible for a national identification database and one of that country’s largest media conglomerates, according to a new report by cybersecurity firm Recorded Future Inc. Both the government agency and the media company dispute the claims.
UK
New ten-year plan to make the UK a global AI superpower
UK Government: Department for Digital, Culture, Media & Sport
The UK today launches its first National Artificial Intelligence (AI) Strategy to help it strengthen its position as a global science superpower and seize the potential of modern technology to improve people’s lives and solve global challenges such as climate change and public health.
Europe
US-EU tech alliance is off to a bad start
POLITICO
@BMoens @laurenscerulus
An attempt to build a transatlantic framework for cooperating on trade and technology looks cursed before it’s even started. Even before a transatlantic flare-up over submarines, which now looks likely to delay the first session of the Trade and Tech Council planned for September 29, Washington and Brussels had widely diverging visions of what they wanted out of this new diplomatic initiative.
Europe Mulls French Request to Delay Trade Talks With U.S.
Bloomberg
@JohnFollain @AlbertoNardelli
The European Union is discussing a possible delay to the first meeting of the Trade and Technology Council that was due to gather in Pittsburgh on Sept. 29 with the U.S. following French outrage over a canceled Australian submarine contract that was scuttled in favor of a new defense pact with Washington and the U.K.
Russia’s ‘Ghostwriter’ hacker group takes aim at German election
POLITICO
@laurenscerulus @livklingert
Having disrupted democratic processes in Lithuania, Latvia and Poland, a young, brazen hacking group linked to the Kremlin has now zoned in on Europe's biggest country, which goes to the polls this week, in a hugely consequential test of the bloc's ability to stop Russian aggressors blatantly targeting its political process. Germany's foreign ministry called out the Russian state this month for being behind a hacking campaign targeting members of its federal parliament and regional parliaments with fake emails — in apparent attempts to hack into confidential information that can be used to destabilize or tilt the election.
Germany’s Far-Right Political Party, the AfD, Is Dominating Facebook This Election
The Markup
@ghongsdusit
Despite its modest size in Germany, the AfD has been remarkably successful on Facebook. Data obtained through The Markup’s Citizen Browser project, in partnership with Germany’s Süddeutsche Zeitung, shows how the AfD has gained tremendous traction on Facebook in the run-up to a historically contentious national election to replace Angela Merkel, the long-serving chancellor, later this month.
Ireland: State’s Cyber Security Centre ‘under-resourced’ to meet its goals
The Irish Times
The State’s cyber security centre is “under-resourced and over-tasked” and does not have the “organisational design or capacity” to meet its goals, a confidential report has found. A capacity review into the National Cyber Security Centre (NCSC) was carried out by consultants between January and March of this year which compared the centre to other organisations of a similar scope internationally.
How the Mafia Is Pivoting to Cybercrime
VICE
@lorenzofb
Police in Europe announced Monday that they had arrested more than 100 people connected with Mafia organizations that were employing hackers to support traditional crimes such as extortion and drug trafficking. This operation highlights a new trend: traditional organized crime groups, such as the Italian Mafia and Camorra, are now dabbling in cybercrime to support their traditional offline activities, according to Italian and Spanish police investigators involved in the crackdown who spoke with Motherboard.
Norwegian Data Protection Authority choose not to use Facebook
Datatilsynet
@bjornerikthon
Director-General of the Data Protection Authority, Bjørn Erik Thon says the authority concluded that the Data Protection Authority should not use Facebook in its communication activities. They believe the risks to the users’ rights and freedoms associated with the processing of personal data through a Page on Facebook are too high
Russia
Navalny’s “Smart Voting” election campaign undermined by fake apps and Telegram channels
Medium
@EtoBuziashvili
On September 6, 2021, Russian media regulator Roskomnadzor blocked access to the official “Smart Voting” website. On September 17, the first day of the three-day voting period, Apple and Google removed the Smart Voting app following threats from Russian authorities that the companies’ local employees would be subject to prosecution. But these were not the only efforts made to throttle the Smart Voting campaign. In May 2021, a Moscow court ordered Google and Russian search engine Yandex to eliminate the term “smart voting” from their search results.
Vladimir Putin is finally getting the Internet he wants
The Washington Post
@AndreiSoldatov @irinaborogan
The Kremlin doesn’t want a Russian version of China’s “Great Firewall,” or to seal off the Runet entirely from the outside world. Instead, Vladimir Putin wants his subjects to rely on Russian-made services and applications, to communicate via Russian social media platforms, to watch videos on Russian-made platforms and to search for information using Russian-provided services. That way, he hopes, they will be dependent on the version of reality the Russian authorities are keen to promote.
Africa
‘There is no private life’: Three Togolese journalists react to being selected for spyware surveillance
Committee to Protect Journalists
@Rozen_J
When Komlanvi Ketohou fled Togo in early 2021, he left behind his home, his family, and his cell phone that the gendarmerie seized when they arrested and detained him over a report published by his newspaper, L’Independant Express. In July, Ketohou, who goes by Carlos, learned that the phone number connected to the device they took may have been targeted for surveillance years before his arrest.
Misc
Facebook oversight board reviewing ‘XCheck’ system for VIPs
Associated Press
Facebook’s semi-independent oversight board says it will review the company’s “XCheck,” or cross check, system following an investigation by The Wall Street Journal into the use of this internal system that has exempted high-profile users from some or all of its rules.
To treat users fairly, Facebook must commit to transparency
Facebook Oversight Board
Last week, new information emerged on Facebook’s ‘cross-check’ system, which the company uses to review content decisions relating to some high-profile users. This information came to light due to the reporting of the Wall Street Journal, and we are grateful to the efforts of journalists who have shed greater light on issues that are relevant to the Board’s mission. These disclosures have drawn renewed attention to the seemingly inconsistent way that the company makes decisions, and why greater transparency and independent oversight of Facebook matter so much for users.
Anonymous' hackers claim to hit website hosting firm popular with Proud Boys
CNN
@snlyngaas
The hacking collective Anonymous last week claimed to have stolen and leaked reams of data held by Epik, a website hosting firm popular with far-right organizations like the Proud Boys. The more than 150 gigabytes of data swept up in the breach shine a light on years of online activities from far-right groups, including those who tried to overturn the 2020 presidential election. While researchers are still sifting through the data, Epik has historically provided web hosting services to an array of conspiracy theorists, and for conservative media networks like Parler and Gab.
These Apps Deliver Food and Misery
The New York Times
@ShiraOvide
Many of the delivery businesses that have sprung up in the last few years make no financial sense and may be turning us into monsters. I’m talking about app-based companies including Uber, DoorDash, Gopuff and many others around the world. They aim to bring us groceries, cooked meals, a home cleaner, cases of beer or a trip across town — all better, faster and cheaper than how we’ve always done things.
Giving AI-generated voices human-like emotion
Axios
@bryanrwalsh
A startup is developing AI voices that can be edited to present different emotional intonations. The voiceover industry — including everything from video games to audiobooks — stands to be disrupted if tech companies can deliver AI-generated text-to-speech voices that can truly mimic human speech.
Inside Amazon’s Department Store Plans: High-Tech Dressing Rooms, Its Own Apparel Brands
The Wall Street Journal
@SebasAHerrera @khadeeja_safdar
Amazon's planned department stores will aim to boost its apparel sales by offering shoppers a chance to try on clothes from its own private-label brands in technology-fueled dressing rooms, according to people familiar with the matter. The department stores, which the online shopping company could open next year, will primarily function as a place for Amazon to sell T-shirts, jeans and other items from its own labels, as well as a mix of outside brands that sell clothing on its website, the people said. Amazon wants to see if the potential department stores can improve the brand recognition of its apparel while addressing some of the irritants of both online and bricks-and-mortar clothes shopping, they said.
A Stalkerware Firm Is Leaking Real-Time Screenshots of People's Phones Online
VICE
@josephfcox
A stalkerware company that’s designed to let customers spy on their spouse’s, children's, or employees' devices is exposing victims’ data, allowing anyone on the internet to see screenshots of phones simply by visiting a specific URL.
What’s Working and What Isn’t in Researching Influence Operations?
Lawfare
@lageneralista
The emergence of a field devoted to researching, and countering, influence operations is something I have watched closely. In 2014, I channeled a fascination with propaganda from the two world wars into researching how the phenomena was changing in a digital age. THe field has come a long way since 2014. But certain pathologies still remain entrenched and hamper effective dialogue and cooperation between key stakeholders. A lack of universal definitions about the problem often means that meetings are spent level-setting, rather than problem-solving.
A generation that grew up with Google is forcing professors to rethink their lesson plans
The Verge
@mcsquared96
The concept of file folders and directories, essential to previous generations’ understanding of computers, is gibberish to many modern students.
New report shows kids see COVID-19 misinfo on TikTok in minutes
Protocol
@issielapowsky
TikTok is pushing COVID-19 misinformation to children and teens within minutes of creating a new account, whether they actively engage with videos on the platform or not, a new report has found.
Instagram Is Doing Grave Harm to Our Generation. We Need Help to Stop It
Time
@DestineeAdams16 @zamaan_qureshi
Like most young people, Destinee quickly learned how to use Instagram for social gain. If she used more than one filter she received more likes, and if she showed more skin, she received more comments. She was obsessed with increasing her engagement—likes, comments and shares—because the more she received, the more she felt she was positively perceived by her peers.
Who’s Who in AI?
Onalytica
Neringa Mikutyte
SwissCognitive is closely watching the cross-industry global AI market – which has notably taken off with Covid. In this time of rapid transition, we all want to gain a clear perspective. What is certain is that a home office doesn’t equate to digitization and that we all want our businesses to be rolling again. That is exactly where AI comes into play – a technology that is practically already available today, yet still has enormous development potential in the future. There is no doubt: there is no company that should let this chance slip away.



Research
Robot Hacking Games: China’s Competitions to Automate the Software Vulnerability Lifecycle
Center for Security and Emerging Technology
@CSETGeorgetown
Software vulnerability discovery, patching, and exploitation—collectively known as the vulnerability lifecycle—is time consuming and labor intensive. Automating the process could significantly improve software security and offensive hacking. The Defense Advanced Research Projects Agency’s Cyber Grand Challenge supported teams of researchers from 2014 to 2016 that worked to create these tools. China took notice. In 2017, China hosted its first Robot Hacking Game, seeking to automate the software vulnerability lifecycle. Since then, China has hosted seven such competitions and the People’s Liberation Army has increased its role in hosting the games.
Physiognomic Artificial Intelligence
Social Science Research Network
@luke_stark @jevanhutson
The reanimation of the pseudosciences of physiognomy and phrenology at scale through computer vision and machine learning is a matter of urgent concern. This Article, which contributes to critical data studies, consumer protection law, biometric privacy law, and anti-discrimination law, endeavors to conceptualize and problematize physiognomic artificial intelligence (AI) and offer policy recommendations for state and federal lawmakers to forestall its proliferation.
Prying eyes and ears: The impact of Facebook’s Project Aria on people's privacy
Journal of Responsible Technology
@AnthroPunk @CatherineFlick
The rapid evolution and spread of digital technology raise various privacy and ethical issues both for those developing technologies and for the public. Some new technology contains small cameras that can be easily disguised in public, with photo and video data that can be recorded, distributed, exploited and combined with previously collected data. A case in point is Project Aria, launched by tech giant Facebook, in which new mapping technology has been combined with augmented reality (AR) glasses equipped with a smart camera and microphones, enabling users to record and track both public and private spaces, and the people within them – including those who may or may not wish to participate. The ethical issues raised by Project Aria are part of the research areas of Sally Applin from HRAF Advanced Research Centres, UK and Catherine Flick from the Centre for Computing and Social Responsibility at De Montfort University, UK. Applin and Flick have published their concerns in a paper in Elsevier’s Journal of Responsible Technology.


Events & Podcasts
The Facebook Files, a Podcast Series
The Wall Street Journal
The Facebook Files, an investigative podcast series, dives into an extensive array of internal Facebook documents that provide an unparalleled look inside the social media giant. The documents were largely written by a group of researchers inside the company whose job was to study the platform’s problems and try to come up with solutions. Together these documents show that Facebook knows it’s causing harm but time and again hasn’t fixed it.
Jobs
ICPC Senior Analyst or Analyst - China
ASPI ICPC
ASPI’s International Cyber Policy Centre (ICPC) has a unique opportunity for exceptional and experienced China-focused senior analysts or analysts to join its centre. This role will focus on original research and analysis centred around the (growing) range of topics which our ICPC China team work on. Our China team produces some of the most impactful and well-read policy-relevant research in the world, with our experts often being called upon by politicians, governments, corporates and civil society actors to provide briefings and advice. Analysts usually have at least 5 years, often 7-10 years’ of work experience. Senior analysts usually have a minimum of 15 years relevant work experience and, in addition to research, they take on a leadership role in the centre and tend to be involved in staff and project management, fundraising and stakeholder engagement.
Project Coordinator: 'Online influence and opinion'
Tactical Tech
Tactical Tech is an international NGO whose mission is to build capacity at the intersection of human rights and technology in order to create more equitable, democratic and sustainable societies. Tactical Tech is looking for a highly committed and experienced individual to come on board as a Project Coordinator for our work on a group of projects under the key theme Influence & Opinion. We are looking for someone who possesses a good understanding of the following topics: misinformation, investigation and media freedom, personal data and human rights.